Davis Cyber Solutions

Enterprise-Grade Cybersecurity for Hot Springs BusinessesDon't let a ransomware attack close your doors. We provide the same vulnerability defense used by Fortune 500s, tailored for Arkansas small business owners.
See Our Plans
Bronze Tier
The Standard Compliance Scan
Satisfies Internal Scanning Requirements (11.2.1). We provide the mandatory quarterly internal vulnerability reports that auditors require for your compliance binder. (Note: Does not replace the External ASV scan).PCI DSS 4.0 Standard Authenticated Internal Scan:
We fulfill the new mandatory requirement (11.3.1.2) for internal scanning. We log in to your network to identify deep-seated vulnerabilities that external scans miss.Full Subnet GHOST Asset Discovery:
We scan your entire IP range to detect "Shadow IT" identifying unmanaged devices, rogue cameras, or forgotten servers connected to your network.Audit-Ready Reporting:
You receive the raw Pass/Fail PDF reports required for your compliance binder to prove you are actively managing vulnerability risk.Remediation Guidance:
We don't just fail you; we provide a clear list of what patches your IT team needs to install to pass.
(Packages starting at $2,500/yr*)
Request a Quote
Silver Tier
The Insurance Shield (Most Popular)
Best for Medical Clinics, Law Firms, and businesses with Cyber Liability Insurance. Includes everything in the tiers above PLUSInsurance Scorecard:
No confusing jargon. You get a clear 1-page summary designed to satisfy insurance underwriters and prove "Due Care."Credentialed "Deep Dive" Scans:
We use administrative credentials to perform a deep inspection of your entire software ecosystem, catching hidden flaws in Adobe, Java, and Browsers that standard scans miss.Configuration Auditing:
Beyond just software patches for PCI compliance, we audit your system settings against industry best practices (CIS Benchmarks) to ensure your passwords and policies are actually secure.The "Triple-Tap" Process:
We scan once to find the issues, provide a prioritized fix list and perform a second "Verification Scan" after patching to prove the risks were removed. This is followed by a "Triple-Tap" 7 Days Later to get the devices that were offline during verification.External Perimeter Check:
We view your network exactly how a hacker sees it from the outside to identify exposed ports and services.
Get a Free Consultation
Gold Tier
The Security Officer
Best for Manufacturers, Logistics, and complex networks requiring aggressive defense. Includes everything in the tiers above PLUSRansomware Prevention Audit:
We specifically check your Active Directory for weak passwords, "Ghost Users," and dangerous administrative privileges that ransomware gangs exploit.Monthly Vulnerability Management:
Hackers don't wait for "Quarterly" reviews. We scan every month to catch Zero-Day threats immediately.Quarterly Strategy Call:
A dedicated review with your leadership to explain your risk posture, plan the next quarter's defense, and budget for necessary IT upgrades.Managed ASC Compliance Coordination
Stop juggling vendors. We coordinate your official PCI External Audit with our certified partners, managing the technical disputes and paperwork so you get your "Pass" Certificate without the headacheContact for Enterprise Pricing
*one time $1,250 set up fee required for all plans
Navigating PCI DSS 4.0 Requirements
Q: What is the biggest change in scanning requirements for PCI 4.0?A: The shift to Authenticated Scanning (Requirement 11.3.1.2). In the past, many businesses only scanned from the "outside in." Under 4.0, you must provide the scanner with credentials (login access) to look inside your systems. This identifies deep-seated vulnerabilities that external-only scans would miss.Q: Is this an official ASV scan?A: Because we are not a ASV vendor we partner with Sectigo to ensure you have access to a complete compliance scan package. We can manage the ASV certification process for you for a small administrative fee. An ASV scan is included in our Gold Plan through our certified ASV partner.Q: What happens if the scan finds a "Fail"?A: For PCI compliance, any vulnerability ranked "High" or "Critical" (usually a CVSS score of 4.0 or higher) must be remediated to pass. Once your IT team applies the necessary patches or configuration changes, we perform a "clean-up" scan to verify the fix and issue your passing report.Q: We use a 3rd-party payment processor. Do we still need these scans?A: Yes. Even if you don't store credit card numbers, your "CDE" (Cardholder Data Environment) includes the computers and networks that transmit that data. If your network is compromised, a hacker could redirect your customers to a fake payment page. Vulnerability assessments ensure your "hand-off" to the processor remains secure.
Q: What exactly is a Vulnerability Assessment, and how does it differ from a Penetration Test?A: Think of a Vulnerability Assessment as a digital "X-ray." It uses automated tools to identify known security gaps, outdated software, and weak configurations. It is designed to be a high-level, frequent health check. A Penetration Test is a "Fire Drill." It involves a human expert actively trying to exploit those gaps to see how far they can get.Request a Quote
About Davis Cyber Solutions
Led by Devon Molina-Davis, CISSP
Founder & Principal ConsultantI founded Davis Cyber Solutions with a simple mission: to provide local businesses with the same level of cybersecurity protection used by Fortune 500 corporations without the "Enterprise-Grade" price.Why?It's because I have the ability to help. I am dedicated to protecting Arkansas business owners from foreign/domestic threat actors.With over a half-decade of experience in IT and Cybersecurity, including a role as an Endpoint Security Engineer at Fortune 500 retailers, logistic companies and hospitals, I have protected networks on a massive scale. Our team has managed security for tens of thousands of endpoints, hunted down hidden threats, and built automated systems to close vulnerabilities before they could be exploited.Our background isn't just in running scans, instead it's in fixing problems. From discovering unmanaged 'ghost' devices to reducing organizational vulnerabilities, our goal has been defined by tangible, measurable risk reduction.I believe that cybersecurity shouldn't be a 'black box' of confusion. You shouldn't have to guess if you are secure. I take a 'Trust but Verify' approach to every engagement using commercial-grade tools (Nessus Professional) to identify risks, and then verifying every fix personally. I don't just hand you a report and walk away. I partner with you to secure your future.CISSP® (Certified Information Systems Security Professional)
AWS Certified Cloud PractitionerBased in Hot Springs, Arkansas, I am proud to serve the Central Arkansas community.Powered by Tenable Nessus Professional Technology
What does your attack surface look like over time?
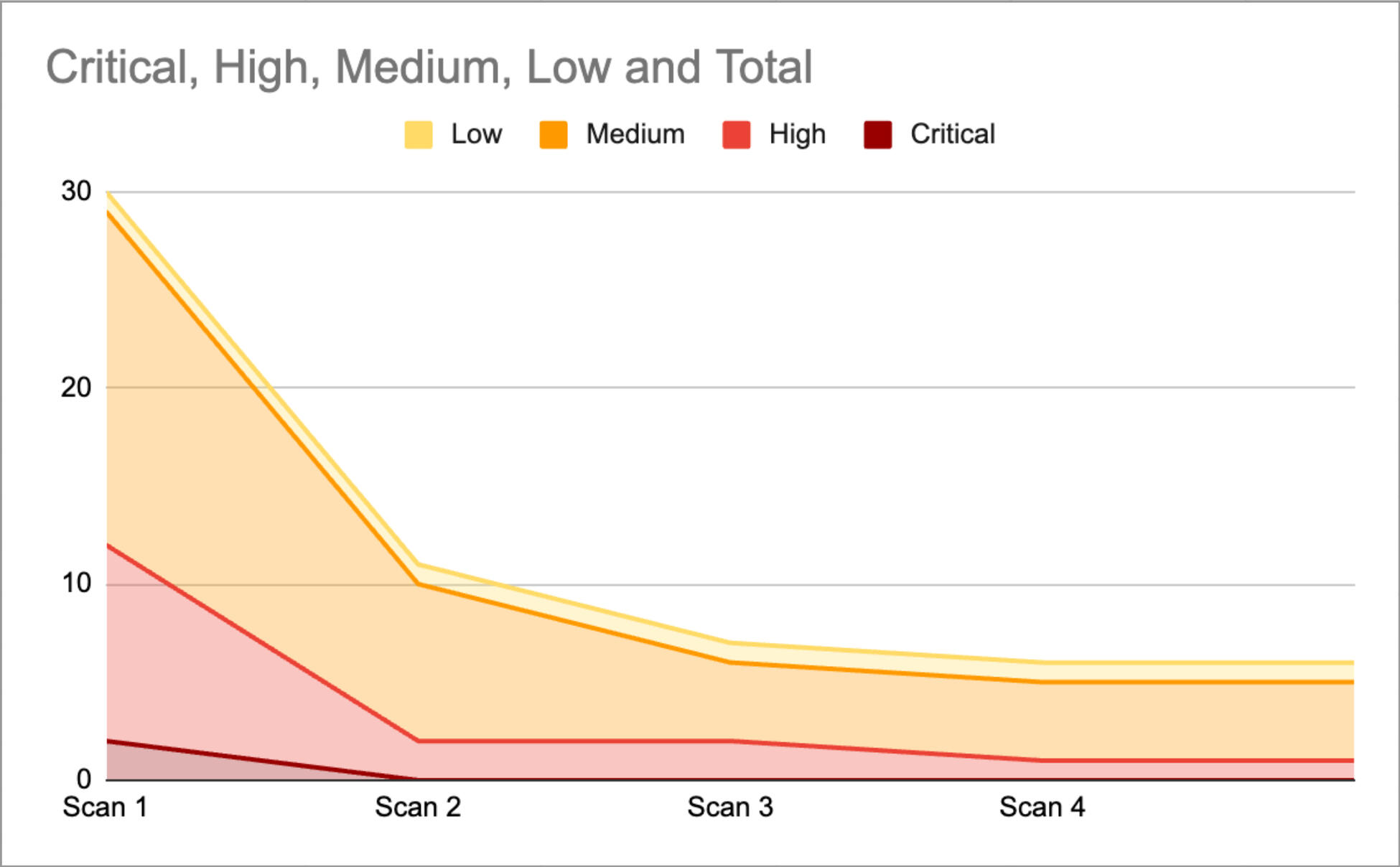
We find the high severity vulnerabilities for your Operations Team
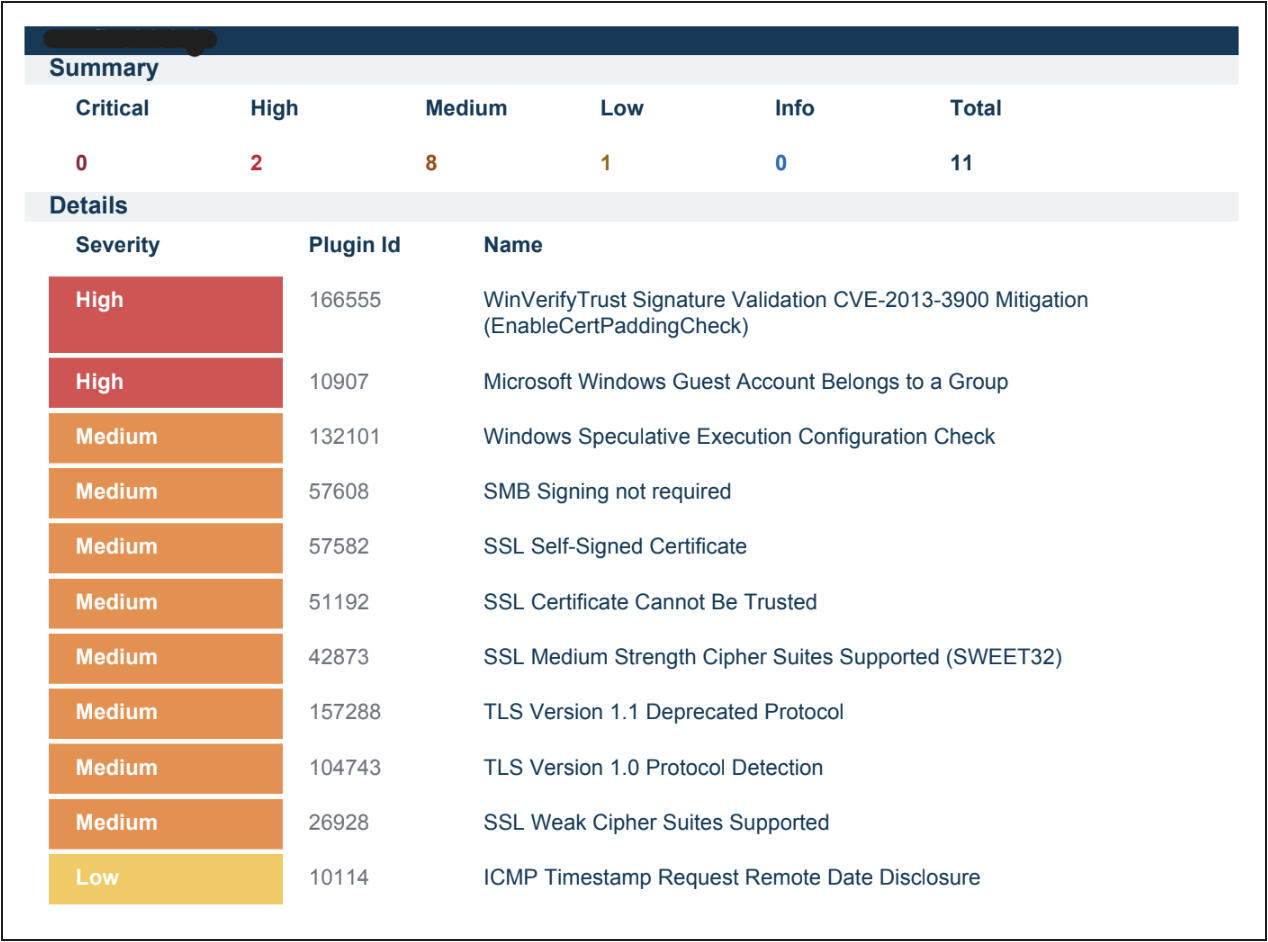
And equip leadership with easy to understand reports.
Ready to secure your assets?
For a free assessment contact us at:
[email protected]
(903) 278-4420
© 2025 Davis Cyber Solutions LLC. All Rights Reserved.